

Distributed denial of service attacks, also known as DDoS attacks, can significantly impact your business or organization’s technological infrastructure. Whenever a DDoS attack occurs, the attacker will deliberately and maliciously send a significant web traffic volume to your website or the systems supporting it. This attack causes the website to not perform at its usual standards, and you will struggle to serve users or customers.
A distributed denial of service attack can be disruptive in the best case and destructive in the worst-case scenarios. It can also have serious knock-on effects on user experience, customer flow, and more. For that reason, it is best to be countered by a distributed protection system based in locations around the world for maximum coverage.
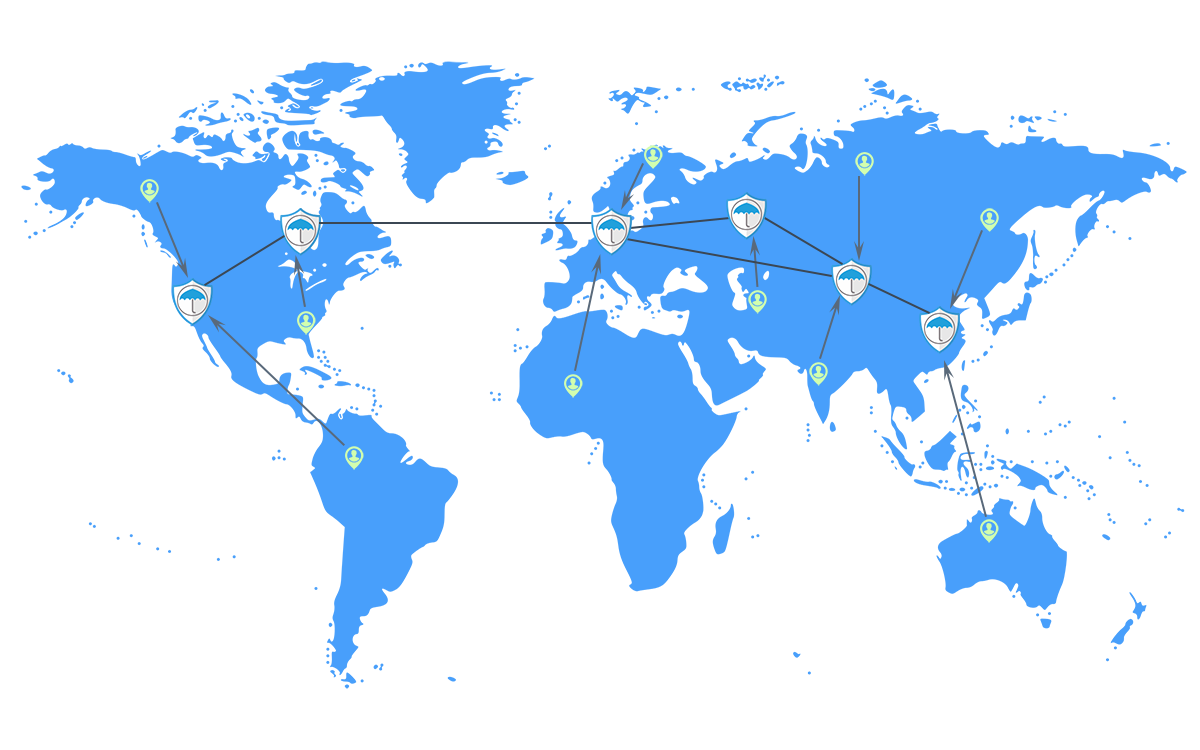
Geo-distribution means that we get to place “scrubbing centres” which are dedicated locations from which web traffic can be analyzed to prevent malevolent attacks coming from locations all over the world. Our centers exist in Europe, Asia, and North America.
There is a simple reason for the geographical distribution: no matter where the attacker directing high volumes of traffic to your website might be, having a regional scrubbing center on hand means that you can mount local defenses effectively and in a timeframe that will defend your website.
All of our DDoS protection tools also come with proprietary software packages. So, no matter the geo-distribution of your scrubbing center, it will benefit from our expertise. Meanwhile, our web filter is maintained regularly to combat the latest threats and stay updated on malicious threats on the Internet.
Secure Socket Layer, or SSL for short, is a major force in Internet security. It is essentially a form of encryption, and it is perhaps the most user-friendly form of encryption, as it is embedded into many URLs through the use of HTTPS. If you’re in the market for web hosting, SSL filtration is one of the most important mitigation technologies to have on your side.
It works by putting incoming traffic through a process of decryption once it arrives at the source. It is then scanned for potentially malicious data – and encrypted again before it arrives at the website in question. And in another form of this service, the decryption element can be removed, and the process can be carried out in an entirely transparent way.
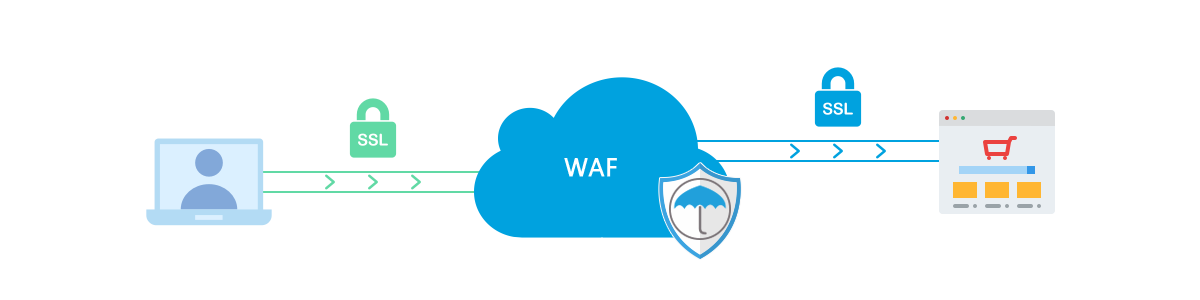
The barriers to set-up for this sort of mitigation device are minimal. The operator of a website will need to give us some basic information, like the private side of their public-private RSA key, as well as their SSL certificate. From there, we can then get the mitigation system set up in a matter of moments.
As well as the technological defenses that SSL filtration provides, it can also act as a deterrent to those who might consider attacking your website. The security certificate’s prominent position in many modern web browsers means that users with both benign and malign intentions can discover with ease that you have this mitigation technology installed, and it acts as a signifier of both trustworthiness and security.
In Internet security, DNS stands for “Domain Name System” – and it is the way in which the URL that the user types into their browser is converted into the technical Internet Protocol, or IP, address on the network. Your DNS, then, is one of the most important nodes in your online architecture.
DNS systems can, unfortunately, fall victim to distributed denial of service (or DDoS) attacks – and that is why mitigation technology like DNS filtering should be installed when the web hosting set up process occurs.

This protection system works by ensuring that a process of switching takes place between the UDP, which stands for User Datagram Protocol, and TCP – which is the Transmission Control Protocol. The aim here is to validate incoming data and filter out traffic, which may be malicious. The process, which affects the pathway between the secure server and the client, is set to happen on an automated basis.
To add an additional layer of safety to a client’s DNS system, we are able to store client domain names on our DNS servers – which feature cutting-edge security technology to further reduce risk.
In an attempt to minimize the impact that this complex system can have on website loading speeds and other aspects of user experience, the software packages we use to ensure the switching process takes place are automated and fast.
The nature of attacks like distributed denial of service attempts and other potential threats from malicious online actors is ever-present. And those who perpetrate these attacks attempt to exploit vulnerabilities, which means they may try to attack your web presence during the night or at a time when you are not as responsive as normal.
As a result, technical support services which operate 24 hours a day and seven days a week are essential – and we offer this service. Specific our staff trained in monitoring for potential problems are on hand at all times and are primed to look for particularly unusual volumes or forms of traffic – and to then act to ensure that the attack can’t take place.
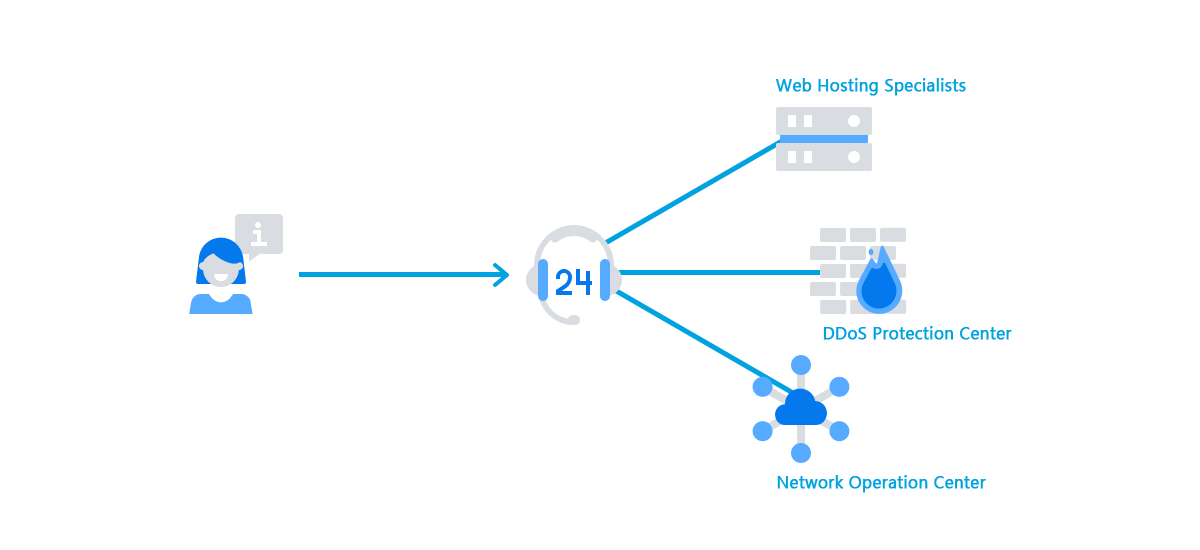
We have several tiers of support available to our customers. We take the view that no Internet Security question is too small or insignificant. So, we have made our customer service agents available through a range of methods like help desk, email, social and more.
For particularly technical questions about DDoS protection, mitigation engineering, and more, our NOC – or network operations center – engineers can provide you with information about the network’s operations, the fixing of vulnerabilities, and much more.
Thanks to these provisions, you can be sure that any problems with your network’s security can be fixed on time to prevent downtime, breaches, and much more.