
DDoS stands for Distributed Denial of Service. A DDoS attack is a deliberate and malicious attempt to break up the normal traffic around a particular target service, network, or server, by overwhelming that target with a wave of internet traffic.
A DDoS attack will be effective by using several infected computers or networks as a base. One useful analogy is to regard a DDoS attack as being like a deliberately engineered traffic jam, filling the highway with traffic, and preventing normal traffic from reaching its destination.
The methods, motives, and targets for a typical DDoS attack will vary, but the focus is usually on attempts to interrupt or even suspend regular services for the target. Such targets are typically those services with high profiles, including credit card banking gateways, banks, or root name servers. DDoS attacks have also been seen in the gaming world.
A DDoS attack is classified as a violation of the Proper Use protocol of the Internet Architecture Board. They are also in violation of the Acceptable Use rules for nearly all Internet Service Providers. They often violate the laws of relevant nations or jurisdictions in which they are carried out.
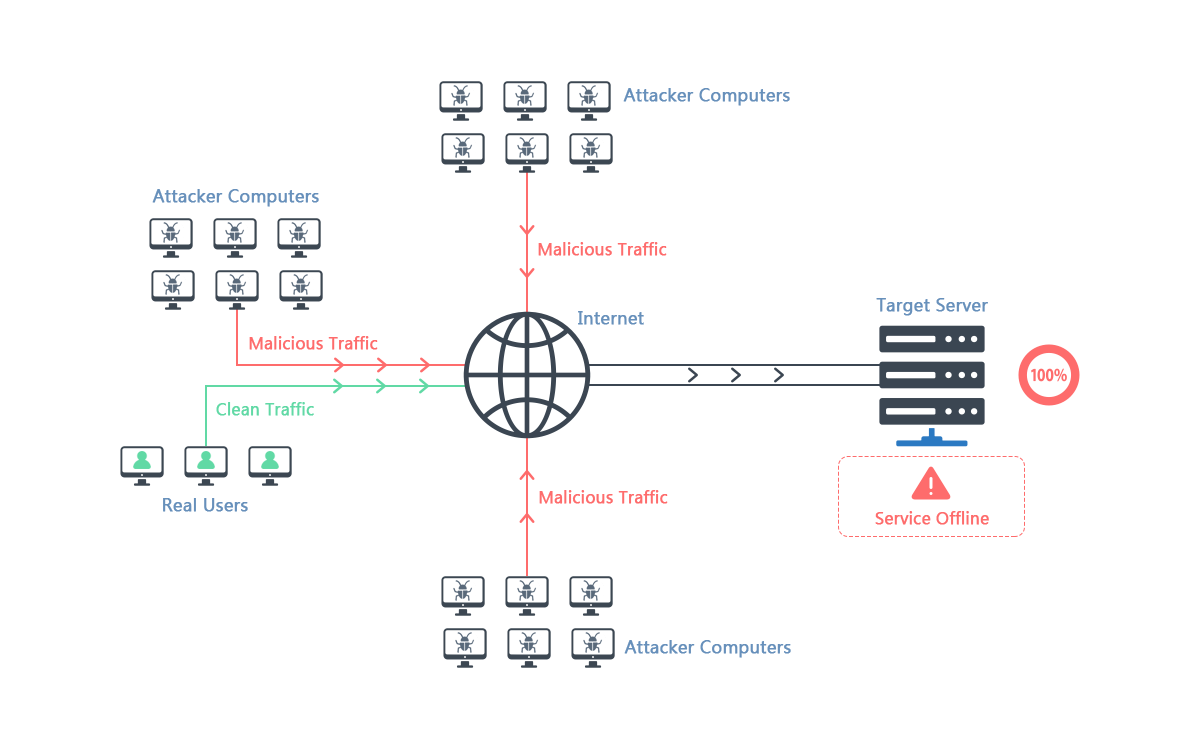
For a DDoS attack to work, the attacker has to win control of an entire network of internet-connected machines. The attack will involve computers and other internet-linked devices being infected with a form of malware, which effectively turns each device into a bot. The attacker will seek to control many such infected devices, which is known as a botnet.
With a botnet set up, the attacker can program the devices by sending new instructions. A DDoS attack will involve targeting the IP address of the victim. Each bot in the botnet will issue requests to the target, which can potentially result in the targeted network or server exceeding its capacity, which leads to disruption of normal internet traffic.
DDoS attacks can be particularly difficult to deal with because each of the bots in the botnet is a legitimate device, making it hard to separate normal traffic from attack traffic.
There are various types of DDoS attacks, all of which work in different ways or focus on different areas of the targeted system, but they come in three main categories.
Application Layer Attacks
These attacks deplete the target’s resources, focusing on the network layer that generates web pages in response to HTTP requests. A typical example is the HTTP Flood, which produces an effect similar to multiple computer users pressing refresh in their web browser repeatedly, causing HTTP requests to flood the target server.
Protocol Attacks
These are sometimes known as State Exhaustion attacks, and this form of DDoS activity aims to exhaust the webserver’s capacity or associated tool, such as a firewall. One example is the SYN Flood, which initiates many contact requests from spoof IP addresses, which are never completed.
Volumetric Attacks
The volumetric DDoS attack is focused on creating maximum congestion by consuming all the bandwidth between the internet and the target. A DNS Amplification is a typical example of this form of DDoS attack. It involves using the IP address of the target to request a response from a DNS server, structured in a way that ensures the targeted DNS server responds with a significant amount of data, which can eventually exhaust the target’s bandwidth.